picoCTF - Forensics in CTF's I
Challenge 1: information
🟩 Easy challenge
Using the hint of the challenge name, and the fact that the challenge is in a image, we can probably check the information of a image file, aka the EXIF data.
Using the exiftool we can extract the EXIF data from the image file.
Now we get the output
% exiftool cat.jpg
ExifTool Version Number : 13.10
File Name : cat.jpg
Directory : .
File Size : 878 kB
File Modification Date/Time : 2025:08:02 18:24:20+10:00
File Access Date/Time : 2025:08:02 18:24:32+10:00
File Inode Change Date/Time : 2025:08:02 18:24:20+10:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.02
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Current IPTC Digest : 7a78f3d9cfb1ce42ab5a3aa30573d617
Copyright Notice : PicoCTF
Application Record Version : 4
XMP Toolkit : Image::ExifTool 10.80
License : cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9
Rights : PicoCTF
Image Width : 2560
Image Height : 1598
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 2560x1598
Megapixels : 4.1
We see in the License section we have what looks like a Base64 string. Once we run that through the base64 tool we get
% base64 -d <<< "cGljb0NURnt0aGVfbTN0YWRhdGFfMXNfbW9kaWZpZWR9"
picoCTF{the_m3tadata_1s_modified}
picoCTF{the_m3tadata_1s_modified}
Challenge 2: Glory of the Garden
🟩 Easy challenge
Using a hex editor or even a regular text editor we can open up the raw contents of the file.
I use GHex but this is personal preference.
Scrolling to the bottom we see this text
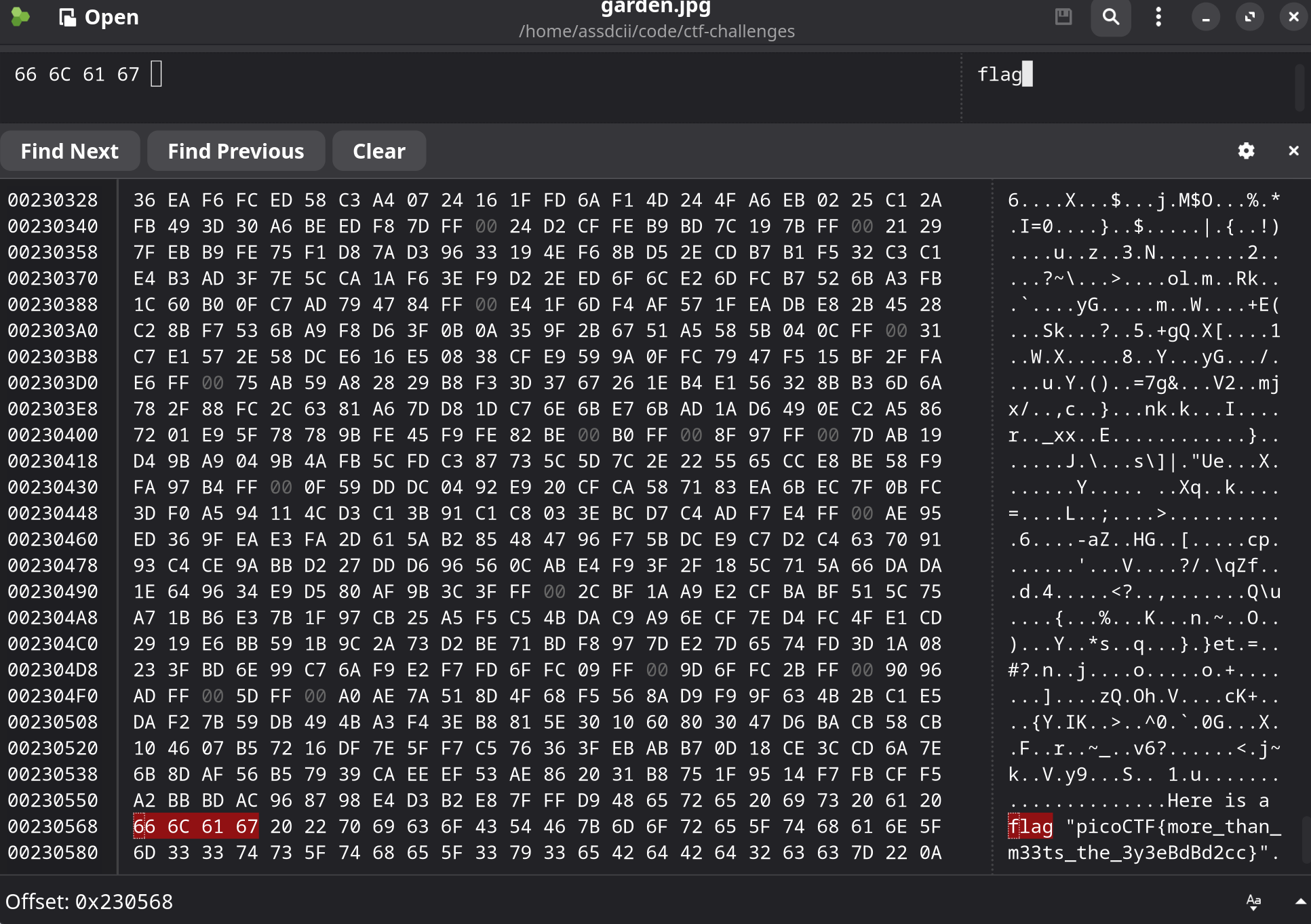
At the end of the image file we can see some plain text reading
picoCTF{more_than_m33ts_the_3y3eBdBd2cc}
Challenge 3: Enhance!
🟧 Medium challenge
Once we download the svg file and try to open it, all we see is a black circle with another little circle within it.
An SVG file is a XML file but is used my programs like web browsers to draw pictures, this is because it stores things like vectors, colour values etc to be able to draw these pictures.
If we open the svg file contents in a text editor, we will be able to see anything including text written in it.
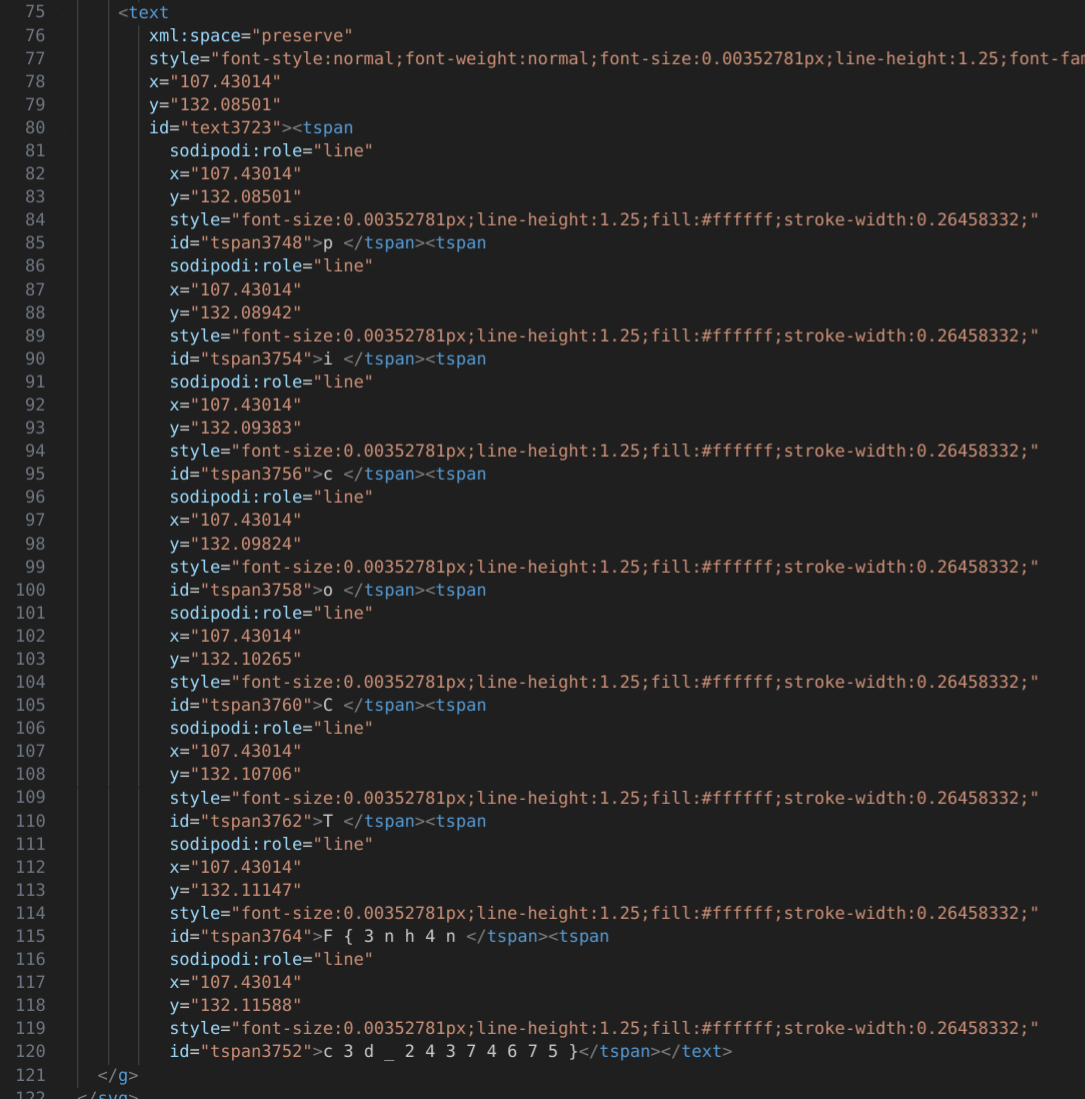
At the bottom of the SVG file we can see some text that look like a flag (the text coloured in white), if we reconstruct it we get the text
picoCTF{3nh4nc3d_24374675}
Enjoy Reading This Article?
Here are some more articles you might like to read next: