picoCTF - Forensics in CTF's III
Challenge 1: extensions
🟧 Medium challenge
We get a file called flag.txt, we open it up and are greeted with a jumbled mess.
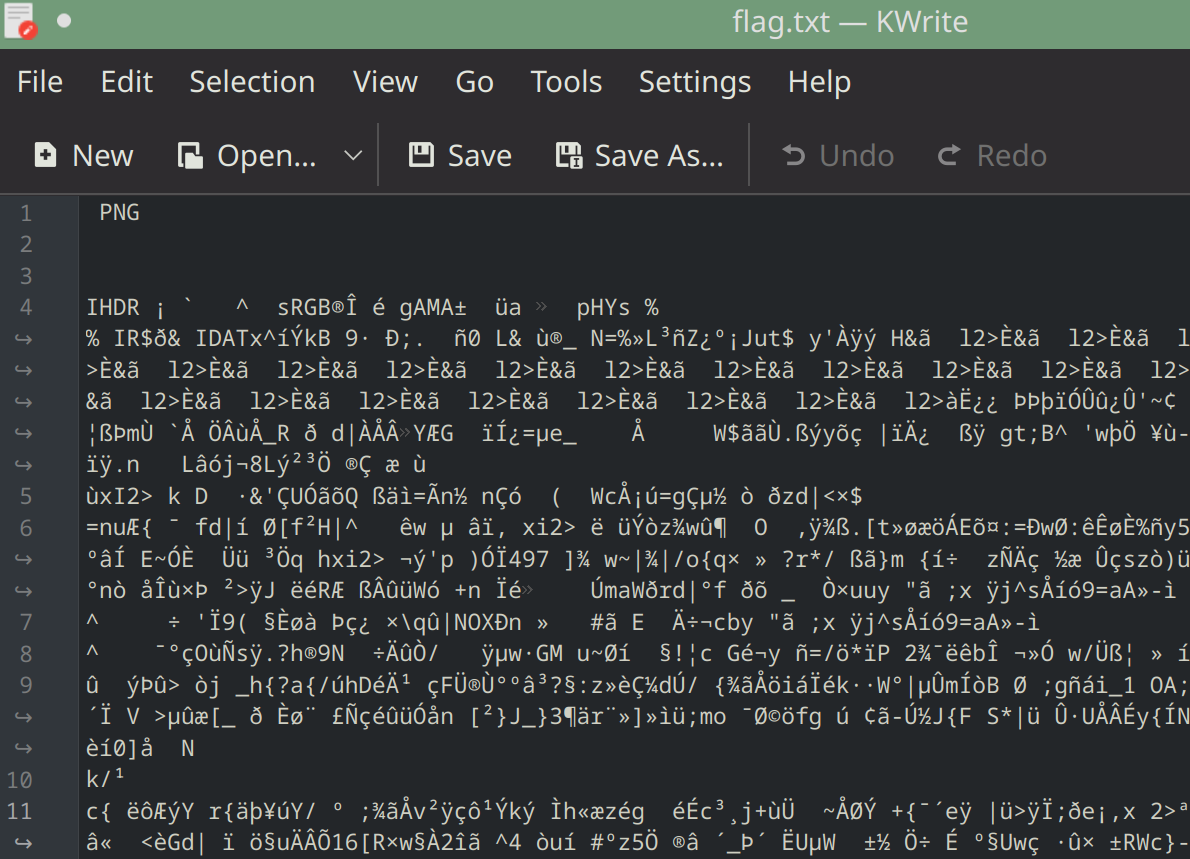
But at the top we find something interesting, its actualy a PNG file. If we replace the .txt extension with a .png, we get the image
Challenge 2: St3g0
🟧 Medium challenge
Using the video in the “Forensics in CTF’s” playlist, we know that there is a Stenography tool called image-stego-tool on github https://github.com/djrobin17/image-stego-tool
Once we download this tool with
% git clone https://github.com/djrobin17/image-stego-tool
Now we can launch the tool with python
python3 stego.py
--Welcome to $t3g0--
1: Encode
2: Decode
2
Enter Source Image Path
pico.flag.png
Enter Password
$t3g0
Decoding...
Hidden Message: picoCTF{7h3r3_15_n0_5p00n_a1062667}
After a couple of guesses we can figure out that the password is $t3g0.
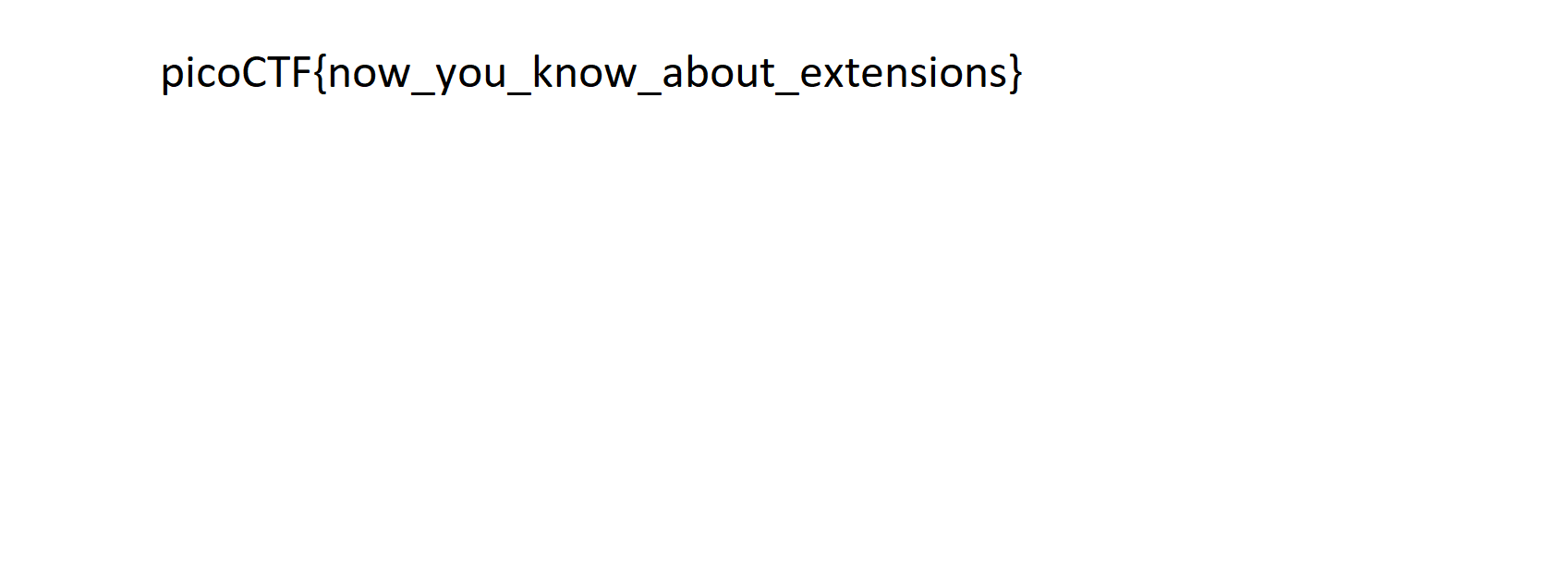
Giving us the flag
picoCTF{7h3r3_15_n0_5p00n_a1062667}
Challenge 3: What Lies Within
🟧 Medium challenge
This challenge might not work if you are using a browser with image tracking content protection, like some Firefox forks. Switch over to a different browser or disable tracking content for the website to work properly.
Again, using the video found in the “Forensics in CTF’s” playlist in picoCTF, we can find a section of the video where the host uses this tool
https://stylesuxx.github.io/steganography/
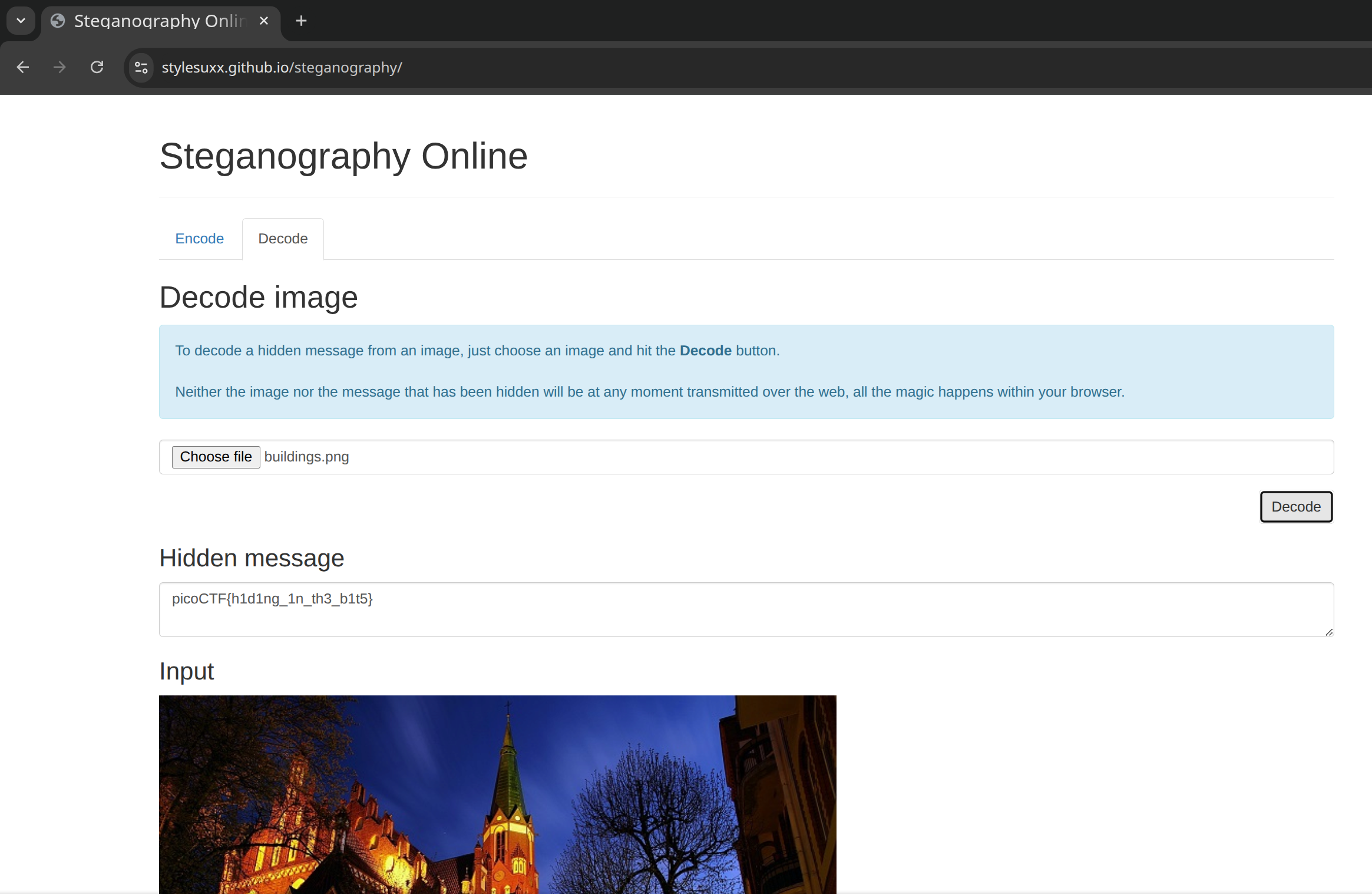
When we decode the image given to us named building.png with this tool we get the secret message, our flag.
picoCTF{h1d1ng_1n_th3_b1t5}
Enjoy Reading This Article?
Here are some more articles you might like to read next: