picoCTF - Forensics in CTF's IV
Challenge 1: Packets Primer
🟧 Medium challenge
Once we open up the network capture .pcap file, if we look at the hex values on the right on the 4th packet in the list. We can see that the flag is in there.
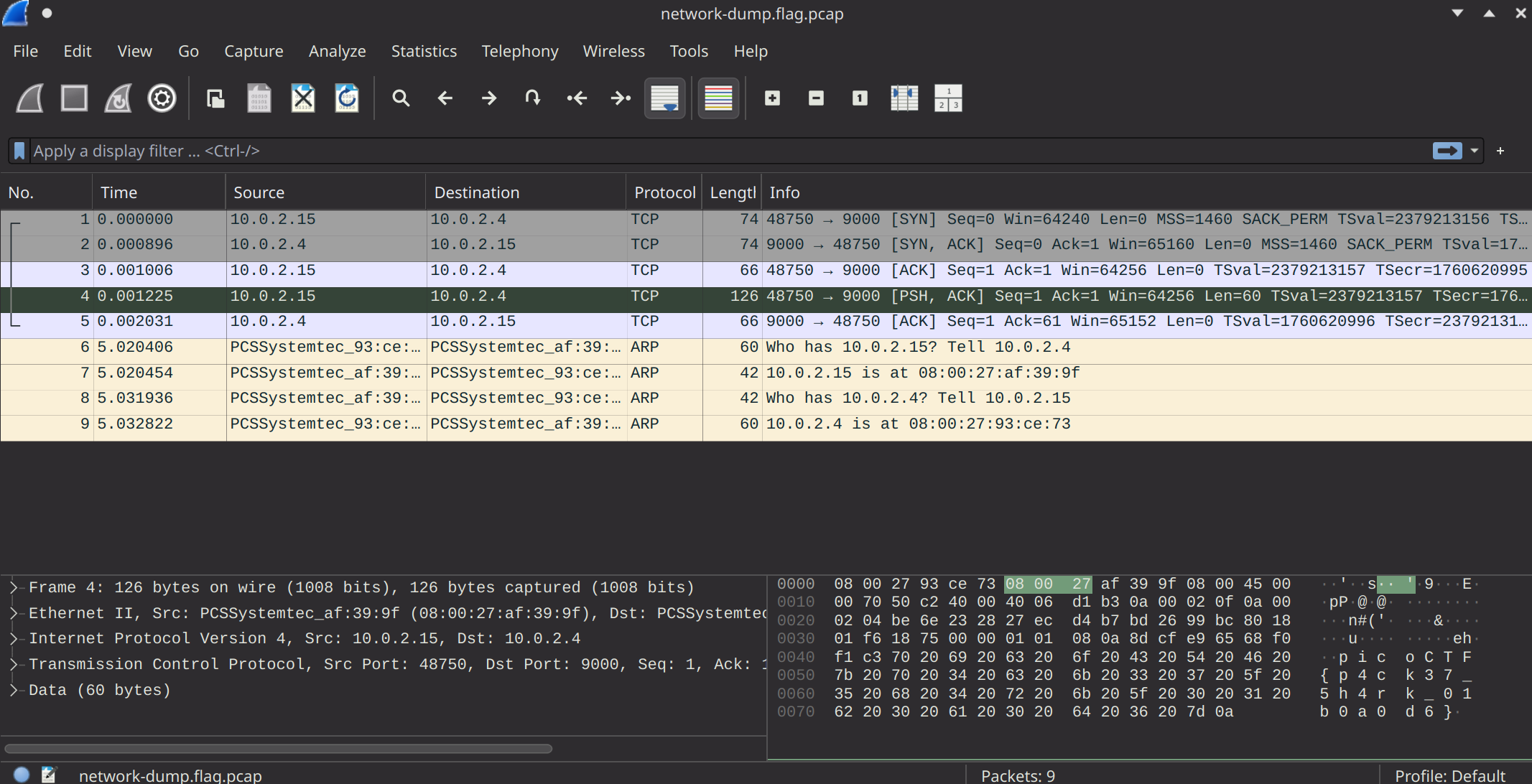
picoCTF{p4ck37_5h4rk_01b0a0d6}
Challenge 2: Wireshark doo dooo do doo...
🟧 Medium challenge
In the packet capture we have lots of HTTP requests, in Wireshark we can filter for the HTTP requests by simply typing “HTTP” into the search bar at the top. Once we go digging for a bit, we will stumble across packer 827
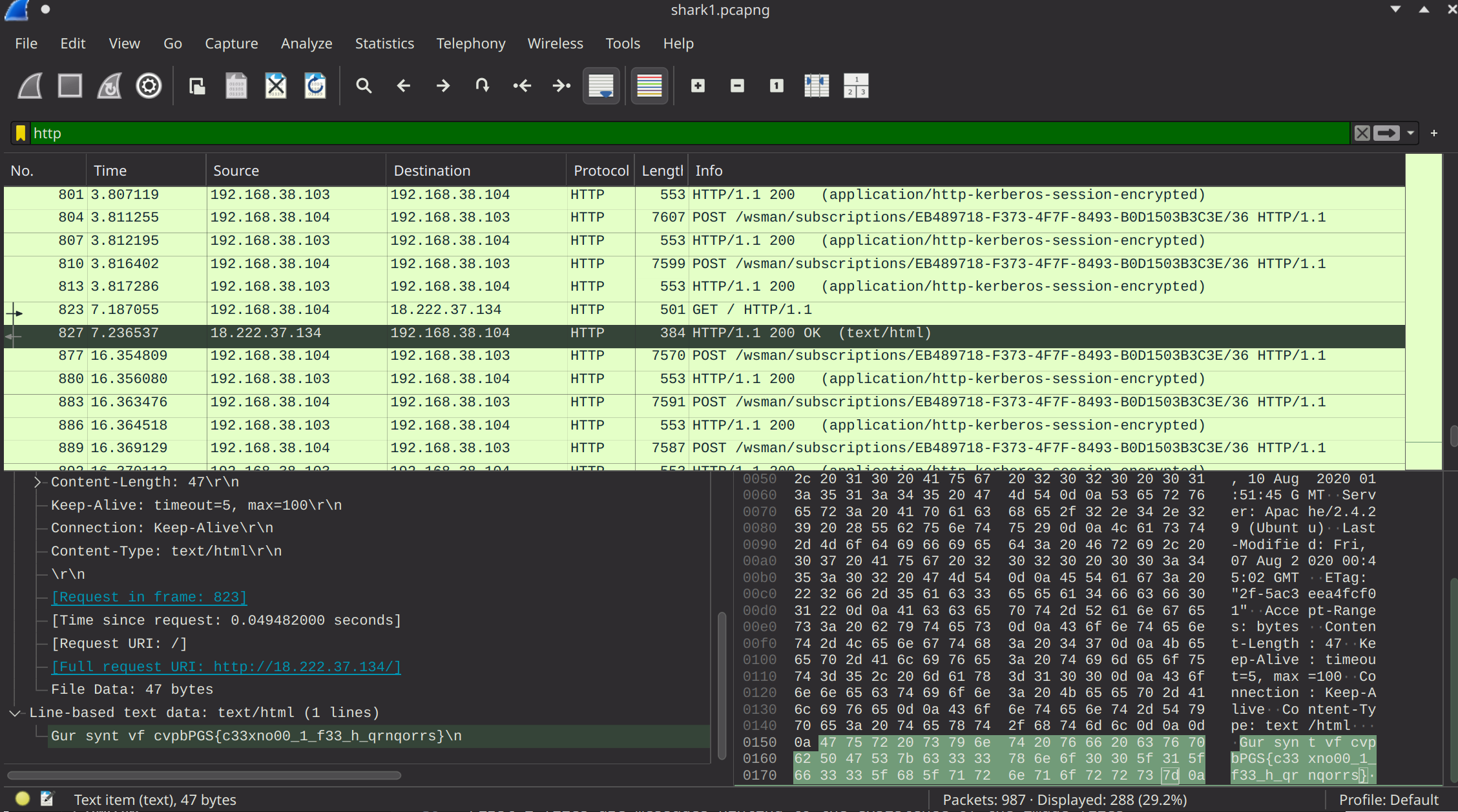
Do you see it? A weird text segment in the packet with our favourite curly braces. But the text segment seems to be encoded in some way.
Using dcode.fr and going to their cipher identifier page, we can see it returns it with a ROT13 cipher. Decoding it as ROT13 will give us the text The flag is picoCTF{p33kab00_1_s33_u_deadbeef}
picoCTF{p33kab00_1_s33_u_deadbeef}
Challenge 3: Trivial Flag Transfer Protocol
🟧 Medium challenge
Upon opening up the file, we are greeted with a series of TFTP messages, also known as Trivial File Transfer Protocol.
Using the tftp filter in the search bar, we can follow along and requests and drown out the other networking noise. The first two files transferred are named instructions.txt & plan.
Using dcode.fr again we can identify that the contents of these files are messages between 2 people, reading
Person 1 instructions.txt
“TFTPDOESNTENCRYPTOURTRAFFICSOWEMUSTDISGUISEOURFLAGTRANSFER.FIGUREOUTAWAYTOHIDETHEFLAGANDIWILLCHECKBACKFORTHEPLAN”
TFTP DOESNT ENCRYPT OUR TRAFFIC SO WE MUST DISGUISE OUR FLAG TRANSFER.FIGURE OUT A WAY TO HIDE THE FLAG AND I WILL CHECK BACK FOR THE PLAN
Person 2 plan
“IUSEDTHEPROGRAMANDHIDITWITH-DUEDILIGENCE.CHECKOUTTHEPHOTOS”
I USED THE PROGRAM AND HID IT WITH-DUEDILIGENCE.CHECKOUT THE PHOTOS
Downloading the files
In Wireshark, if you capture a TFTP file exchange, then you can download all the files by going to
File ==> Export objects ==> TFTP…
Looking through the downloaded files we have picture1.bmp, picture2.bmp, picture3.bmp, program.deb as well as our instructions.txt and plan
Inside the program.deb file, we can see that this is steghide (0.5.1-9.1). Steghide is a stenography tool used to hide text and data within an image that is encrypted with a password. So it’s safe to assume that the attacker used this tool to encrypt their message within one of these image files.
Putting the pieces together, the attacker used the steghide tool to embed a message into an image file, and now we have to guess what file as well as what the password could be.
If we look back at the messages they exchanged between each other, we can see an odd phrasing in their message.
WITH-DUEDILIGENCE
There is a hyphen in-between the two words, I thought WITH would be the password, so let’s try to decrypt the message from one of these files with the password DUEDILIGENCE.
% steghide --extract --stegofile picture1.bmp --passphrase DUEDILIGENCE
steghide: could not extract any data with that passphrase!
% steghide --extract --stegofile picture2.bmp --passphrase DUEDILIGENCE
steghide: could not extract any data with that passphrase!
% steghide --extract --stegofile picture3.bmp --passphrase DUEDILIGENCE
wrote extracted data to "flag.txt".
% cat flag.txt
picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}
picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}
Alternative solution
Instead of being smart, you could instead just hit it with a hammer enough times for it to break, aka Brute-forcing it.
Using a tool called stegseek we can brute force images that, we think, are encrypted with steghide in seconds. Like so.
To run it, type in the command
% docker run --rm -it -v "$(pwd):/steg" rickdejager/stegseek picture3.bmp crackstation.txt
Where picture3.dmp is the image file and crackstation.txt is my wordlist that I’m using.
PS C:\Users\rain\Desktop> docker run --rm -it -v "$(pwd):/steg" rickdejager/stegseek picture3.bmp crackstation.txt
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "DUEDILIGENCE"
[i] Original filename: "flag.txt".
[i] Extracting to "picture3.bmp.out".
PS C:\Users\user\Desktop> cat .\picture3.bmp.out
picoCTF{h1dd3n_1n_pLa1n_51GHT_18375919}
Enjoy Reading This Article?
Here are some more articles you might like to read next: